How to Stop the Meltdown and Spectre Security on INTEL and other Processors and Android Devices
Vulnerabilities in modern computers leak passwords and sensitive data.
On May 14, 2019, Intel published information about a new subclass of speculative execution side-channel vulnerabilities known as Microarchitectural Data Sampling. They have been assigned the following CVEs:
- CVE-2018-11091 – “Microarchitectural Data Sampling Uncacheable Memory (MDSUM)”
- CVE-2018-12126 – “Microarchitectural Store Buffer Data Sampling (MSBDS)”
- CVE-2018-12127 – “Microarchitectural Fill Buffer Data Sampling (MFBDS)”
- CVE-2018-12130 – “Microarchitectural Load Port Data Sampling (MLPDS)”
Important: These issues will affect other systems such as Android, Chrome, iOS, and MacOS. We advise customers seek guidance from their respective vendors.
Update: As of February 20, Intel has released stable microcode updates for Skylake, Kaby Lake, and Coffee Lake—that’s the 6th, 7th, and 8th Generation Intel Core platforms. PC manufacturers should begin rolling out new UEFI firmware updates soon.
If you did install a UEFI firmware update from your manufacturer, you can download a patch from Microsoft to make your PC stable again. Available as KB4078130, this patch disables the protection against Spectre Variant 2 in Windows, which prevents the buggy UEFI update from causing system problems. You only need to install this patch if you’ve installed a buggy UEFI update from your manufacturer, and it isn’t being automatically offered via Windows Update. Microsoft will re-enable this protection in the future when Intel releases stable microcode updates.
In 2018 it was found Meltdown is a hardware vulnerability affecting Intel x86 microprocessors, IBM POWER processors, and some ARM-based microprocessors. It allows a rogue process to read all memory, even when it is not authorized to do so.
Since the issues—dubbed Meltdown and Spectre—exist in the CPU hardware itself, Windows, Linux, Android, macOS, iOS, Chromebooks, and other operating systems all need to protect against the first exploits that have begun circulating. And worse, plugging the hole can negatively affect your PC’s performance.
These hardware vulnerabilities allow programs to steal data which is currently processed on the computer. While programs are typically not permitted to read data from other programs, a malicious program can exploit Meltdown and Spectre to get hold of secrets stored in the memory of other running programs. This might include your passwords stored in a password manager or browser, your personal photos, emails, instant messages and even business-critical documents.
Meltdown and Spectre work on personal computers, mobile devices, and in the cloud. Depending on the cloud provider's infrastructure, it might be possible to steal data from other customers.
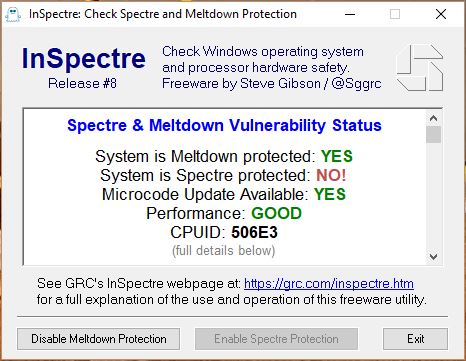
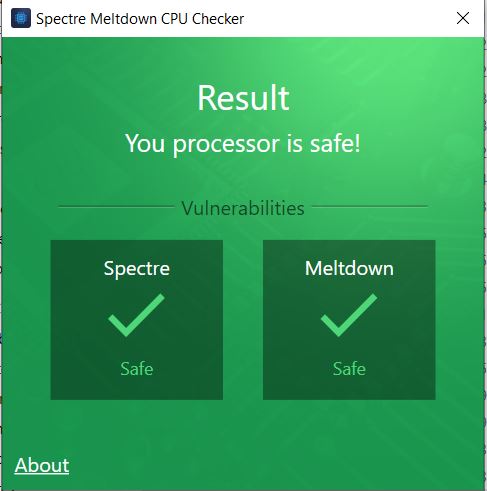
Software to check if your computer is safe
If you see “Performance: GOOD”, you have a modern PC with the appropriate hardware features and you shouldn’t see a noticeable slowdown.
Download here / ashampoo also have a checker (click the image below to get)
Meltdown
Meltdown breaks the most fundamental isolation between user applications and the operating system. This attack allows a program to access the memory, and thus also the secrets, of other programs and the operating system.
If your computer has a vulnerable processor and runs an unpatched operating system, it is not safe to work with sensitive information without the chance of leaking the information. This applies both to personal computers as well as cloud infrastructure. Luckily, there are software patches against Meltdown.
Spectre
Spectre breaks the isolation between different applications. It allows an attacker to trick error-free programs, which follow best practices, into leaking their secrets. In fact, the safety checks of said best practices actually increase the attack surface and may make applications more susceptible to Spectre
Spectre is harder to exploit than Meltdown, but it is also harder to mitigate. However, it is possible to prevent specific known exploits based on Spectre through software patches.
Leslie Culbertson at intel says "Following Google Project Zero’s (GPZ)* disclosure of speculative execution-based side-channel analysis methods in January, Intel has continued working with researchers across the industry to understand whether similar methods could be used in other areas. We know that new categories of security exploits often follow a predictable lifecycle, which can include new derivatives of the original exploit."
"As part of this ongoing work, today Intel and other industry partners are providing details and mitigation information for a new derivative of the original vulnerabilities impacting us and other chipmakers. This new derivative is called Variant 4, and it’s being disclosed jointly by GPZ and Microsoft’s Security Response Center (MSRC).*"
If you're looking to see if your PC is impacted and whether patches are available, here's a list of major manufacturer pages to keep an eye on...
- Acer
- ASUS
- Dell
- Fujitsu
- HP
- Intel
- Lenovo
- Panasonic
- Microsoft
- Toshiba
- Vaio
- Intel® Core™ i3, i5, i7 processors (45nm and 32nm)
- 2nd, 3rd, 4th, 5th, 6th, 7th and 8th generation Intel® Core™ processors
- Intel® Core™ X-series
- Intel® Xeon® processor 3400, 3600, 5500, 5600, 6500 and 7500 series
- Intel® Xeon® processor E3, E5 and E7 family
- Intel® Atom™ Processor C, E Series, A, x3 and Z Series
- Intel® Celeron® Processor J and N Series
- Intel® Pentium® Processor J and N Series
- Intel® Xeon Phi™ Processor 3200, 5200, 7200 Series
| Intel | |
| Microsoft | |
| ARM | |
| Red Hat | |
| Apple | Vulnerability Response |
I have recently changed my chrome browser for Comodo and also installed its Security suite
Welcome to Smart Gadgets Tech Show!
Thanks for stopping by. I welcome your thoughts, comments and tips. Please use the contact form to get in touch.